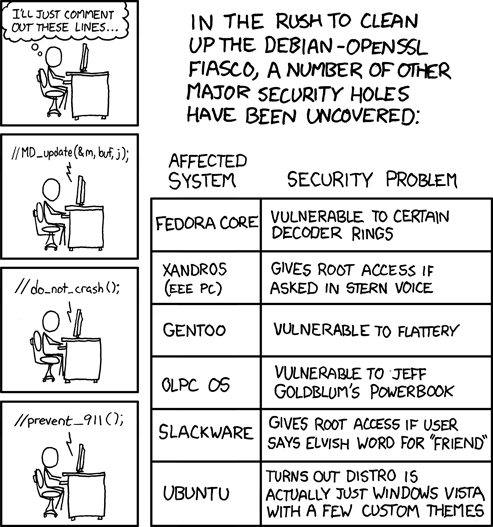
10th article of this successful series.
From Kevin Mitnick's Twitter status, this one really made me roll on the floor :
Old Dilbert still applicable in many SMBs security ;-)
A tweet from ISSA_France:
— Gargamel, how did you find our village?
— Google Maps.
Showing posts with label rofl. Show all posts
Showing posts with label rofl. Show all posts
Sunday, August 11, 2013
Monday, March 25, 2013
Security ROFL 9
French communication through SSID labels (from Guillaume Germain's Twitter):
— The girl next door is so sexy!
— The girl next door is not interested.
Traffic sign jacking (from the blog Si vis pacem para bellum):
The complexity of using PGP. The bad guys don't use that tool anymore ^^ The good neither. (From XKCD)
A sorry but so plausible story of an engineer outsourcing his own job to China by himself. And comments about logging systems. (From Aaron Weiss @ eSecurity Planet)
The pretty naughty story of what happens when you post a job offer through unprofessional people...
French swindler promising to fix any PC, including defective hard drives, through voodoo :-D
— The girl next door is so sexy!
— The girl next door is not interested.
Traffic sign jacking (from the blog Si vis pacem para bellum):
The complexity of using PGP. The bad guys don't use that tool anymore ^^ The good neither. (From XKCD)
A sorry but so plausible story of an engineer outsourcing his own job to China by himself. And comments about logging systems. (From Aaron Weiss @ eSecurity Planet)
The pretty naughty story of what happens when you post a job offer through unprofessional people...
French swindler promising to fix any PC, including defective hard drives, through voodoo :-D
Tags:
job search,
outsourcing,
rofl,
seduction,
ssid,
traffic sign,
voodoo,
xkcd
Tuesday, October 30, 2012
Security ROFL 8
- French public job platform going unavailable because of too many requests, on the very day people are asked to update their personal situation to get unemployment benefit. The screenshot below reads "Our services are currently unavailable because of a high level of request. We kindly ask you to excuse us. We advise you to connect later." Either they're getting DoS'ed or they just self-slashdot themselves.

- Hackers Reveal How They Accessed Syrian President Bashar Assad's Email Using World's Worst Password. The password, of course, was 1234.
- Dilbert's "preventer" Mordac goes crazy:
- Security technologies are even in video games nowadays : Blizzard inserts watermarks into all game screens so that screenshots allow them to track (identify, at least) users.
Tags:
password,
rofl,
slashdot effect,
watermark
Thursday, September 6, 2012
Security ROFL 7
- [EN] XKCD always so strong on sarcastics:
- [RO] In the rush to advertise their new Internet Explorer 10 browser, it seems Microsoft has (unwillingly?) compared what's not to be compared. They advertise their rendering engine as faster than those of Google and Mozilla, which is true only because the default config for Internet Explorer allows for a direct access to the graphic card hardware acceleration, which can be problematic. When compared with the same configuration, browsers are, as usual: Chrome >= Firefox >>> Internet Explorer.
- [FR] Le spam nigérian le plus poétique (et drôle).
- [EN] Tax havens among the most popular hangouts for Apple's Safari browser. Just take a look at the chart ^^
- [EN] Fun and unusual HTTP response headers. My favorite is "PoweredBy: Rats in our Basement" ;-)
Sunday, June 10, 2012
Security ROFL 6
- 10 (or so) of the worst passwords exposed by the LinkedIn hack, like "ihatemyjob", "fuckmylife" or "123456" through Anton Chuvakin's G+.
- Using tax refunds to steal money from taxpayers ;-) Tax Return Identity Theft from Bruce Schneier's blog.
- Displaying password in the TV news is no good idea ;-) from the Front Line Sentinel blog.
- Movie Hacking vs Real Hacking, from the Saturday Morning Breakfast Cereal webcomics.
- Dilbert's use of users' private data :-D
- And finally the eternal lesson from the Demotivators :
Monday, June 4, 2012
Epiphany: Free Software = Lower Entry Barrier = Greater Risk of Project Failure
Discussing with a friend lead me to this epiphany: the reason why Free/Libre/OpenSource software is not used enough in traditional companies is that they invest too little in it. Not in money, but in time, thought and human resources.
Since FLOSS has a very low entry barrier (starting from just zero, up to prime class paying service from companies such as IBM), it tends to attract people and companies that want to invest very little in it. That's why they fail to make a great use of it.
Mem: I think there's a business model in just selling GPL software, without any added value, with the argument that the buyer will be more motivated to implement it well ;-)
Tags:
leadership insights,
open VS closed,
opensource,
rofl
Monday, January 2, 2012
Kevin@Exploitability: End of Year Tale, Yet a True Story
This article is a translation of [FR] Petit conte de fin d'année, mais histoire vraie quand même, on Kevin's Exploitability blog. I found it an amazing example of how social engineering things is easier than technically cracking them. The author gave me his permission for this translation:
End of Year Tale, Yet a True Story
In this end-of-year period, let me propose you a little tale that goes beyond IT and security. Or not.
This story happened a few years ago and no name will be given.
So, once upon a time, there was a mall, just like so many others, with a jewellery store inside it. This jewellery store looked like an 'L'. The vertical stroke was open on the shopping arcade, with the cashier desk in the middle, and the bottom stroke had a second desk, dedicated to repairs.
A | V: victim
R | C: main desk
C C | R: repair desk
A |
D `-----+
E R|
R|
+-----------+
The week-end before Christmas, lots of people crowded the arcade and the jewellery store. As often happens, in order to be up to the mark for these additional customers, a few interims were helping with the sales. They were dressed with sober white shirt and black trousers.
Hereupon, with the help of an accomplice, I've sneaked to the top of the shop, also dressed up with a white shirt and black trousers, hidden by a sweater. I've soon noticed a customer holding out a repair bill for a jewel. Once out of my sweater, I approached her and asked her how I could help. Discussed, checked that her repair bill had been paid and let her wait patiently glaring at new year's new collection. Back in my sweater, I got to the bottom desk to ask for the jewel.
They gave me the jewel upon presentation and verification of the repair bill and I managed to discretely get out of the jewellery store on the side opposite to the customer. Thanks to the crowd, the customer did not see me leave, and the legit vendors did not catch the trick.
So I got out of the jewellery store with a splendid necklace adorned with rubies inside my pocket.
[Little notice for people concerned with my integrity: my honesty being limitless, I went back into the store to return the necklace to her owner, so this is a morale tale, with a happy ending :-)]
Being on an IT security blog, what can we tell?
End of Year Tale, Yet a True Story
In this end-of-year period, let me propose you a little tale that goes beyond IT and security. Or not.
This story happened a few years ago and no name will be given.
So, once upon a time, there was a mall, just like so many others, with a jewellery store inside it. This jewellery store looked like an 'L'. The vertical stroke was open on the shopping arcade, with the cashier desk in the middle, and the bottom stroke had a second desk, dedicated to repairs.
+-----+
V |A | V: victim
R | C: main desk
C C | R: repair desk
A |
D `-----+
E R|
R|
+-----------+
The week-end before Christmas, lots of people crowded the arcade and the jewellery store. As often happens, in order to be up to the mark for these additional customers, a few interims were helping with the sales. They were dressed with sober white shirt and black trousers.
Hereupon, with the help of an accomplice, I've sneaked to the top of the shop, also dressed up with a white shirt and black trousers, hidden by a sweater. I've soon noticed a customer holding out a repair bill for a jewel. Once out of my sweater, I approached her and asked her how I could help. Discussed, checked that her repair bill had been paid and let her wait patiently glaring at new year's new collection. Back in my sweater, I got to the bottom desk to ask for the jewel.
They gave me the jewel upon presentation and verification of the repair bill and I managed to discretely get out of the jewellery store on the side opposite to the customer. Thanks to the crowd, the customer did not see me leave, and the legit vendors did not catch the trick.
So I got out of the jewellery store with a splendid necklace adorned with rubies inside my pocket.
[Little notice for people concerned with my integrity: my honesty being limitless, I went back into the store to return the necklace to her owner, so this is a morale tale, with a happy ending :-)]
Being on an IT security blog, what can we tell?
- I played the role of a rogue proxy between a client and a server, in order to intercept authentication credentials.
- The end-of-year overload prevented detection of the rogue proxy (if you can't erase logs, just drown them!)
- The customer did not consider authenticating the server. Think http"S" or typosquatting. Just a little reverse-engineering was enough.
- Finally, the true server granted trust just because of a cookie (the repair bill). A double authentication would have been better: repair bill + national ID card, for instance. The bill, seemingly at the name of a woman, should have raised eyebrows. An authentication cookie for entering and making operations (asking for the status of the repair), with an additional authentication for the handover of the payload, remains an interesting option.
- The extraction of the payload was hooded in a most standard data packet: me, a casual customer, with a grey sweater attracting no suspicion nor attention from legit vendors. To extract data, cypher them (SSL flow) !
Tags:
non-it security,
rofl,
security insights
Friday, December 23, 2011
Security ROFL 5
[FR] Remotely hacking a car is possible!
[EN] Stop to the installing woes, 9€ to get your PC installed, in Romania
[EN] US Nuclear Chain of Command, xkcd comic strip
[EN] Manual Override, xkcd comic strip
[EN] Unpickable, yet again an xkcd comic strip
[EN] Technology organization leadership charts, on Michael Krigsman's blog
[EN] 3D Printer, xkcd comic strip about new forms of spam
[EN] Alarm Geese, blogged by Bruce Schneier
[EN] Stop to the installing woes, 9€ to get your PC installed, in Romania
[EN] US Nuclear Chain of Command, xkcd comic strip
[EN] Manual Override, xkcd comic strip
[EN] Unpickable, yet again an xkcd comic strip
[EN] Technology organization leadership charts, on Michael Krigsman's blog
[EN] 3D Printer, xkcd comic strip about new forms of spam
[EN] Alarm Geese, blogged by Bruce Schneier
Saturday, March 12, 2011
Security ROFL 4
- [FR] This is not the SSH 0day you're looking for, about a fake SSH exploit.
- [EN] Flower sites hit hard by Valentine’s Day.
- [EN] UK Immigration Officer Puts Wife on the No-Fly List.
- [EN] An Update is Available for Your Computer, through [RO] That's how it goes with updates, the piece of comics below:

- [EN] Unsecured IP Security Cameras, which I guess you can verify by yourself.
- [FR] On mikropikol.net, the following comic strip:

Tuesday, January 4, 2011
Security ROFL 3
- Not meant to be funny, Michael Krigsman's Ten great software glitches for 2010.
- Young Man in "Old Man" Mask Boards Plane in Hong Kong, on Bruce Schneier's website, good occasion to remind that Beyond Fear is a good reading, far beyond ITsec people.
- [FR] Videos of a French senator trapped into answering IT questions asked by journalists. He doesn't know a clue about it, and he's in charge of the debate on the neutrality of the Internet...
- [FR] Cartoon about airport security:

- Do you remember Thierry Shaker ?
- Sure, the boy who enjoyed frightening every girl out there, always trying to grope! What does he do now?
- He became an airport security guard...
- The first truly honest privacy policy, underlined by many blogging sites.
Tuesday, November 2, 2010
Security ROFL 2
- A gang of thieves armed with a powerful vacuum cleaner that sucks cash from supermarket safes has struck for the 15th time in France.
- Remote Printing to an E-Mail Address, Bruce Schneier notices that it's an opportunity for spammers :-D
- xkcd cartoon: Exploits of a Mom
- Pirated Software Could Bring Down Predator Drones, which were so funny it weren't so pathetic.
- Finally, let's not forget a lolcat: Iz ok.. we’re Veeganz.
Thursday, October 28, 2010
Fun fact: Facebook Bug in Handling Who Accesses Photos
I just experienced a funny bug: Facebook lets me view photos of someone who is not a "Friend" anymore :-)
OK, it's not in every case, it's just when I had written comments on a photo and someone writes additional comments.
Say I have written a comment in March, on a photo by a friend named Alice (pseudo) :

And then Alice and I stop being "Friends" in Facebook. She doesn't allow anyone but her friends to access photos, so I shouldn't have access anymore. But today someone else writes a comment on that same photo and I receive a notification.

Let's click on the link to Alice's photo. Nice, I can view that old photo again! That I should be let in to see that photo and any additional comments is subject to discussion.
However, the big bug is that I can click on "Back to Album" and I get the complete album, which I certainly should not:

I don't know whether that's a common case or just a kind of local bug or exception...
OK, it's not in every case, it's just when I had written comments on a photo and someone writes additional comments.
Say I have written a comment in March, on a photo by a friend named Alice (pseudo) :

And then Alice and I stop being "Friends" in Facebook. She doesn't allow anyone but her friends to access photos, so I shouldn't have access anymore. But today someone else writes a comment on that same photo and I receive a notification.

However, the big bug is that I can click on "Back to Album" and I get the complete album, which I certainly should not:

I don't know whether that's a common case or just a kind of local bug or exception...
Tags:
facebook,
rofl,
social networks
Tuesday, September 14, 2010
Security ROFL
Let's have some fun about security.
- Exploitability: Truecrypt will never be the same, ya dun goof'd!, an article about the use of a modified version of Truecrypt to recover passwords from the Truecrypt users.
- [SP] Detenidos los gerentes de una empresa que vendió 'software' envenenado a 1.000 empresas, the managers of a company that sold software pre-programmed to fail have been arrested.
- Hi & Lois cartoon, about children being smart about using the internet to unlock a parent-protected device ;-)
- [FR] DNS-Rebinding : Accès aux interfaces d'admin des box Internet, from BlackHat 2010, using DNS to hack into ADSL boxes.
- Film industry hires cyber hitmen to take down internet pirates, by DDoS attacks.
- Is This the Most Ridiculous ReCAPTCHA Image Ever?, with a ridiculous captcha contest encouraged by the blogger.
- [FR] CensorCheap, l'extension Firefox qui ambitionne de surveiller la censure du net, about a Firefox extension that allows to monitor government censorship of the network.
- Security blunders 'dumber than dog snot', at NetworkWorld, self-explaining.
- Buyer Beware: Lock Expert Picks High End Lock, Exposes Major Security Flaw, about a high-tech fingerprint lock that you can pick with just a needle. Be sure to watch the first video.
Thursday, August 5, 2010
Fun Fact: Wrong Sense of Rotation for Deming's PDCA Wheel
Have you noticed how many times management consultants draw the PDCA wheel so that the way to climb up the hill is ACDP and not PDCA?
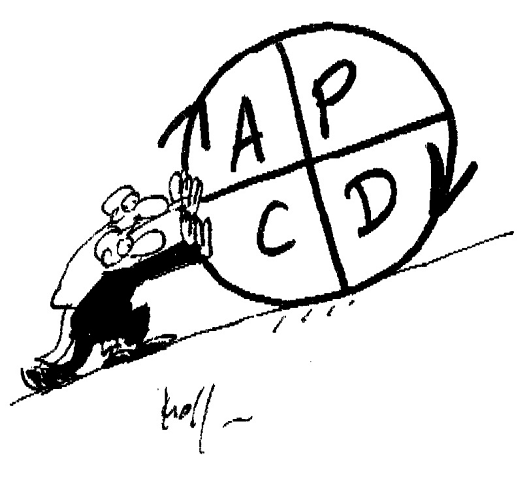

This picture from [GE] Paeger Consulting.
Wednesday, April 28, 2010
Fun fact: Google search ratios about problems, by OS
Search pattern | Number of results | Ratio of "problems" |
| "windows 98" | 21,900,000 | |
| "windows 98" problem | 6,770,000 | 30.91% |
| "windows millenium" | 291,000 | |
| "windows millenium" problem | 77,500 | 26.63% |
| "windows xp" | 124,000,000 | |
| "windows xp" problem | 61,400,000 | 49.52% |
| "windows vista" | 80,900,000 | |
| "windows vista" problem | 88,200,000 | 109.02% |
| "windows seven" | 2,900,000 | |
| "windows seven" problem | 551,000 | 19.00% |
Saturday, April 17, 2010
Hacking a speed cam
France nowadays is full of speed cameras serving car owners huge fines and the ability to loose one's driving license faster than ever. The rebellious French all look for a way to sidestep those speed limitations. Here's a very clever one [FR], though it will never work. And it's a good laugh anyway.
Wednesday, March 24, 2010
Saturday, December 19, 2009
1-factor authentication in the Matrix
I just remembered the way Seraph tells Neo in the Matrix "You do not truly know someone until you fight them." and I was trying to sort the fight that follows into one of the typical categories of authentication:
-+- The little joys of security-thinking ! -+-
- Check what someone has.
- Check what someone knows.
- Check what someone is.
- Neo is the One because he knows he is the One.
- Being the One, Neo knows he is the best kung fu fighter.
- Knowing he is the best kung fu fighter, Neo is the best kung fu fighter.
-+- The little joys of security-thinking ! -+-
Tags:
rofl,
two-factor authentication
Thursday, December 3, 2009
Common antivirus products disabled within minutes
It was the subject of a contest organized by the French IT (and other disciplines) engineering school ESIEA. Results are available as slideshows at this address.
Summarizing roughly, the most common antivirus products (McAfee, Norton = Symantec, Kaspersky...) can be disabled within minutes by a clever virus maker.
Summarizing roughly, the most common antivirus products (McAfee, Norton = Symantec, Kaspersky...) can be disabled within minutes by a clever virus maker.
Thursday, October 1, 2009
F!%#¤ cryptic logs! [Bruce Schneier fun]
I couldn't get an idea of what all that logfile meant. Not binary, but not readable... Until I backed out from the screen:
c:::c:ccoccccocooocCooCcocCooCCCCCCOOOCOOOCOO88COOC@888o8C:.:. ..... .. ... . . coo:@@8@8@8@888888888888
::cccc:cocccccccooCooCocCoooCCCCCCCOOOOOOOCOO@8COC@8OOCCOc:. . . ........ :..... .. . oo.@8@@8@8@888888@8888
::cc:cccocccccoooocoCCooCoCCoOOoOCCOOOOCOOOOO@OO8CCCoCo8o . .. .:::.::.::. .. . . C88@8@@@8@@88888888
::cc:cccccoc:ocoooooCCcCCooCCOCCCCOO8OOCOOCOCOoOC:o8ooc: .....::. ::..:::.o.::..:. . ... . o888888@@@8@@888888
:ccccccocccccoooooCoCCcCoCoCCOCCCCOO88COOCOOC8OCoC8oco: ....::::.:.:.:::.::::::: . ..::COC8@@@@@@@@@@8888
c:c::ccococcccoooCoCCcoOCCCCOCCCOOO88OO8OOOO@CoOCcCo:. . . .....::.:::.:.:c.::cc::o:.. .. . cCoO@@@@@@@@@@@8@@
:c::ccccccc:ccCooCoCCcCOCCCCCCCCOOO@OOC8OOOOCoCc:O8: . . ......:::.:.::.:c:::.oc::cCc::::..... ..oO888@@@@@@@@@@@8
:c::cccccccccoocoCoOoCOCoCCCCCCOCO8O8OOCOOCoCoOOCCC ......c...:cccCccoccoc:o.:::oocc.:co:: . .... .cc@@@@@@@@8@@@@
c::cccccco:coCcoCCoOoOOCCCoCCCOCO888OOOCOO:oCC8CC. ....:::::cccCcCoooOoCoo:ooocc:coc::.... .. .@@@@@@@@@@@8@@
c:ccc:coocccoCcooCoCoOCcoOCCOC8CO88OC8CCOCcoC8@C: . .......:cCCcc:o:oCCoOOCoCcCCoCcccoc:::::.. . o8@@@@@@@@@@@@
c::cccooccccoocCCCCCCOCoCCOOCOOCO888OOOOO.ooOCC . . ..... ..:ccoCCccoCOooooooCooCCoccc::::::..... .O@@@@@@@@@
::cccccccccoocoCCCCoCOooCOOCOOCCOO8OO8o8ocooCO .::. ..:.:.:oCooooC:c::cO8OCcoCCcoCc::cco:.::::... @@@@@@@@@8@
:ccccoccccooocoCooOcCCoCCCCC8CCOOO8CO@CC:cooC. . ...:..:c:::oCCooCCCCCcoCOCooCOooocooco:::c::::. . @88@@@@@@@@
:cccccccccoooCCCoCOoOCCCCOoOCCO888COOCco:Ooc . ..cc.:::.cCcc:::: oCOooCoCOCCCCOCoOoCCoCCoo:ococ:::.:. ..O@@@@@
ccc:ccoccccCcCoCcOCOOCCCCOoOCCO888CCC8::cC: ..:: ..:::ccco:coc ccCOCOoCCCCOOCOOCoCcCOCocoCCccccc:.... c8@@@@@@
cc:cococc:cocCooC8C8CCoOCOCOCOOO8OCO88::.:: ... .::..:cCCocOC.::ooOooOOCCCOCCOCCoCCoccCocoCooo:::.. C@@@@@
cc:ococcc:ooooocCOcOCoCCoOO8C8OCOCOCC:..cc . ....:. ...::cCCCCoCCCCoc:OoCCCOCOOCCCOCoooCCooooCcccc::.. :C8@@@@
c:cocooc:cooooooOC:CCoOCCCOCOOCOOCCoC...: . ..:cCo. ..c:coCCocCoCOOooOCCCOCOOOCOOCCCOooCCooccc.::.::. C@@@
c:coococccCoooooOCoOCoOCOCOCOOOOCCCCc .. . .. :::..:c. ..:::cooooCCCO8ooOOOCOCOOO8CCCCCCCCCococcccc::: . @@@@
ccocccCccoOoocoOO:8OcOCCCCOC8OO8CCoo : ...::.c::::coCCCCo:::oo:oCOCOCo8CCCCOCOOOOOOOOOCOCCCooooococc::: @@
:cococcccCoooooOCCOCC8oOCCOO88OOOoc:.. ..:.:ccoCoCCCCOCO8O8Ooc:cooCCOOOCCOOO8OOOO8O8COOOOOCCCooCoooooccc:.. o8@@
cococccccOoooooOoOCoCOoCCOCOOO8OCc.... ..:ccoooCCOCCCOO888OO8CCooocooC8OOCOOO8OOOOOOOOOCOOOCCCooooCoocoC:... @@@
cococooccCcCcoCOoOCoCOCCCOOOCOO8c..: .c.ccooCoCCCOOOOOOOOOOCCCCCoooCCOOO8OO8OOOOOOOOOOOOOCCCooCooooCccc:... @@@@
cocccoccoooCooOCoOCCOCCCO88OOOCO..:. ...occoooCCCCCOOOOOOOO8OO888OOCCoCOOO88OOO8888OOOOOOOOOOCCoooooCCCoc:... @@@
occcccccocCooo8CoCCCCCoCOCOCOO@C.:. .:cc:cooCCCCCOOOOOOOOOOOO8888OOOOCOO88OOO888OO88OOOOOOOOCCCCoCooococc:....C@
cccoocccooOocOOoCCCoCCCCOcCO8O@c:. . :c:cccoCCoCCCCOOOOOCOOOOOO8OOO8OOOOO888888888O88OOOOOOOOCOCCooooooooCo::.. C
cccccoccooocoCoCOCCCCCCCCoC8O8O.. .::coccooCCoCCOOCOOOOOO8OO8OOO88888O888888OO88O888OOOOOOOOOOCCCoCCooooocc:... 8@
cccCoccooCooCOoCCCCCCCOOCOO8C@o. . :::ccccooCCCCCCOOOOOOOOO8888O88888O8888888O88OO8O8OOOOOOOOOOOCCCoCCooooccc:. :@@
ccococcooCooCCc8CoCoCOCCC8OOOO:: . ..::coocoCCCCCCOOOOOOOOO88888888888888888888OO88O8O8OOOOOOOOOOCCCCCCCoooCcc:.. @@@
occccoocCocCCoCCoCCCCCCOC8OO@o.: ..:cooocooCCCCCOCOOOO8OO8888888888888888888O88O88888O88OOOOOOOOCCCoCCoooCoc:. O@@
ccccccocCoooC:CCCoCOOCCCOCOO8o . .:ccooocoCCCCCOOOCOOOO8O8888888888888888888OO888OO8OOOOOOOOOOOOCCooCCCooCoc::. o@
cccocoocCoCoCcOCCoCOOCCCOC888c. ..::cooocCCCCOCCOOO8OOOOO8888888888888888888888888888OOOOOOOOOCOCCCCCCoooCoo:... :
cccocooCCocOCCCOCCCCCoCOOCC8C. .c:oooo:CCCCCOOOOOOOO8888888888888888888888888888888O8OOOOOOOOOCCCCoCCCCCoooo. @@
ccoccooOooo8COCCoCCCCCC8COCCc ..c:ooCo:CCCCOCOOOOOOOO888888888888888888888888888888OOOOOOOOOOOOCOCooooCooco: . C
ococcocCCooOCCOCCCCCCCCOCCOC: . .::coooccCCCOOOOOOOOCOO88888888888888@888888888888888OOOOOOOOOOOOCOCCCCoCCCoo:. . C@
ooococooCcCOCCCCCCOOCCOCCCCO. ...ccoocoCCCCOOCOOOOOO88888888888888888888888888888888888OOOOOOOOOCCCoCoCoCcoo .. o@
oocoooooCoOCCCCcCOCCCCCCCCC: .::cooCccCCCOOOOOOOOO88888888888888888888888888888888888OOOOOOOOOOCCCCCCCCooc:... .@
cocoCoocCCCoCOCooCCoCOCCCC8. .cocooccCCOCCOOOOO8O8888888888888888888888888888888888OOOOOOOOOOOCOCCoCCCoCc:. . @
occocoCooCCoCCCCCCOCCOCCCC ::ccoccoCOOOCOOOOOOO88888888888888@888888888888888888888OOOOOOOOOCCCCoCCCCCc::. . 8
ocoCoCoCCCooCCCCCoCCCCCCCO . ::ccCccoCCCOOOCOOOOOO88888888888888888888888888888888OO8OOOOOOOOOOCCCCoCCCCoc:: o
cooooCcCCCoCCCoCCCCOCoCCCC .:ccoocoCCCCCOOOOOOOO8O8O88888888888888@888888888888O8OOOOOOOOOOOOCCCCCCCCCcc :.. :
coocoocCoCCOCCcCCCCOCCCCoo .:::cocooCCCCOCCOOOOO8OO8888888888888@8@@@888888888888OO8OOOOOOOOOOCCCCCCCCCCc .. .
coCooocCCoCCoooCCCCCCCCCCo .:.:coccCCoCOCOOOOOOOO8888888888888888888888888888888O8OOOOOOOOCOOOCCCCCCCCoc:. . :
ocococoCCoCooooCCoCCCCOCCo .::cocoooCOCOOOOOOOOO88O88888888888888888888888888O888OOOOOOOOOOOCCCCCCCCCCcc....
oocCCooooooCCoCoCCCOCCoCo . .:coccCCCCOOOOOOOO8OO8O8O888888888888888888888OOOOOOOOOOOOOOOOOCCCCCCCoCoo:. ..
oocCocooCCoCCoooCCCCCCoCo ...:cCccCCCCOOOOO8O8888888888888888888888888888O8O8OOOOOOOOOOOOOOOCCCCCCCCoc:: ..
ocoCcoooCoCCoCoooOCoCCCCc ... . .:ccccCoCCOOOO888O8888888888888888888888888888O8O8OOOOOOOOOOOOOCCCCCCoCooc:...
ocoocooCooCooCoCCCCCCCCo: .. .ccc:cCoOOOOOO88O88888888888888888O888888888888888OOOOOOOOOOOOOCCCCCCCCoc::... .
ooCoccCooCooCCCCCCCoCCCo: ..:c::oCOOOOOO88888888888888888888888888888888O888OOOOOOOOOCOOOOCCCCCooooc::.. ..
coocooCooCoCoCCoCCCCOCCC: ..::.coCOOOO8O8O8888888888888888888888888888888O888OOOOOOOOOOOCOCCCCCCoccc.:.
coocoooooCcCoCoCCCOoCCcC: .::.:oCOOOO88888888888888888888888888888888888888888OOOOOOOOOOOCCCCCCooccc.:. ..
cooooCccooCocoCCCOCCCooo: . .:o:.COOcoCCOOOOO88888888888@88888888888888888888888O8OOOOOOOOOCCCCCCCCoc::... .
cocoCocoocoocCoCCCoCooooc .. .cc:c8C:coCCCOOO8888888888888@@8@8888888888888888888O888OOOOOCOOCCCOCCCc::.... .
oocoocoooooccCoCCooCoCCoc. .. .:cc::c. occoCOCOOOOO888888888@@8@@8888@88@888888888888O88OOOCOCCCCCOCCoc.c. . ..
cooCo:oocCocoCCCCoCCoCCc. . .:c:....ccCoccoCCocCCO88@888@@888@88@888888888888888888888OOOOOCCCCCCCoCc:: .: .
ocooocoooCcoooCCCoCoooCc .:::..:o::ocoCcooooooOO888888@8888888888@8888888888888O8888OOOOCCCCCCCoo::. . . .
coCoooocooooooCCCoCocoo: .. .:c: ::..:ccCcc:ccccoooCC8O@88888888888888O8@8888888888OOOOOOOOCCCCCCoCo::. . .
coocooocCccooCCCCCOcoCo: .:: .cc ::::::.::.Cc.c:::oocOOC888888888OO8COooO8OOCCCOOCOOCCooCOOOCCCCCoo:c.. :..
ooooocccocoCoCCCoCCcCCc:... ccc ..cc .coccCCc.....co:::cooo::888888888OoCCCoo@8ocoCCooOCCoCocoO8OOCCCooc:c. . . ...:
ocococooccoooCCCoCooCoc: :oCo :o: :ccCCc.. . .. .ccooCCoOO88888888COC::COc.ccoCocoooooCocoO8OCoCoccc:. ...
coococcoooccoCCoCCooooo. :::o :c:.cocoo.. :O8cc::co:o:cCCCOOOOO8888OOOOcoCc.coc::cccccCooccocCOOoCoccc:.. . .
ooocccccoocooCooCCoCooo.. . ::: :c.:ccccc.cCC@@.: ::.o:coooOOC88OOOOCOOOCocc:ccoccCoocoocccc:coCcooocc:. .
cocoocccocooooooCCoooo: o: .:c .:c:ocoooc:oCC88c. @: Coco.coCOO88888OOOOCCooc:..cccco::cccoccccccocooccc::.. .
cccooccccoooC:oooooooo:. oo:ccc. . cccCooCoo:oCCO8::. o@@8ooccoOO8888OOOCCoc:cocCc: .::c::.c:c:c:cccccccco.. ... . .
ccccccoccooooocCCccococ: .CC.cCo. ::ocCoCoooc:cooCCo.coo.@8@ooC:oO88O88OOCooocCCoo.8C:o::..:c::Co:c:::occccC. .:. ...
ccccccoccoooocoCoccoocc. cOC.cC8. .cc:CCCcoCoccooooCCooccococoOccO8OO888OooCcOOo::C@:o. ....ocoCoooc:oocccC.. ... ..
ccooccoccoooocoCocooccc. oCocco@ .cccCCoCCCCocoCoCoCOCoOoocoCOcoO888888CoOCoOocOO8Cc: ooCo8..ccCCCCc:ccccoo. .. .
cocccccccoooooooocooccc. CcCoooc :occCoCCCoooooCCCoCCCCOCCCOCOcoOO888OOCCOoOo:C88@oc COo:@@ :ooCCCCc:cocc. .. .c:
ccocccccccooccoooooocc:c O:CCoCo. :ocoCCoCCCCCCCCCOCOOCCCoCCOoc:CCOOO8OOCCocOCCo:C8O:o. :o88CcccoCoCCoccooc. . ...:ccc.
occcccccocCcoooooooCc:cc OO88OCO..oo:oooCCCCCCCCOCOOCCCCCCCCcoccCOO8OOOCoCooOOCCCOCoCc:::OOCoCc:oCCooCoccCC:. ....oCocoC
ccccccccccoccooooCooccco oC888O8..cocCCCCCOCCCCOOOOOOOOCCCCoooo:COOOOOOCooooCCoCoCoCCCoooCOCoocoooCCCCoocoo:. ..:oc:cCo
cccccccccooccCccoocoocco oO8888@..occooCCCCCCOOOOOOOOOOOOCCCooccCOOOOOCCoCoCoCCCoCCCOC8OCoCCoo:ooooCCCoocoo:... .occCoCC
ccccccoccocccoccoococcoc c888888 :ocoCCCOCOOOOOOOOOOOOOOCCCoo:oOOOOOOCCCCoCCCOCCCCOOO8OCCCCooCCooCCCCCCoCo:....:ccooC88
ccccccccccoccooooocooocc :O88O88 cocoCCCOCCOOOOOOOOOOOOOCCoCocoOCCOOOOCCCoCOOCOOOCOOOOOCCCoooCCCCoCCCCCCCc: . :.oCoCO8
ccccccccccccccooocooCocc..OOCO88 .oocoCCOOCOOOOOOOOOOOOOOOCooccoCOOOOCCCCCCCOOOOOOOCCOOCOCCCCCCCCCCCCCCCoCo: . ..cCOoC88
cccccccccccoCoooocooCocc..88OCO@ cccoOoCOOOOOOO8OOOOOOOOCooocoCCOOOOCCCCOCCC888OOO8OOOOOOCOOCCCOCCCCCCCooC: .:oCOOOCCOO
:cccccccccccoocooooCCooc. COCoCo.::ccCCCOOOOOOO888OOOOOOOooCo:oCCOCOOCCCCCCCCO88888O8OOOOOOOOOOCCCCCOCCCCoC: :oCCCOOOo8O
:cccccccccooccoococCoCoo. CCCOCo .:ocCCCOOOOOOO888OOOOOOOooCocoCOCOOOOooCCCCCO888OOOOOO88OOOOOOCCCCCOCCoCoC:.oo8CoOOOC8C
cccccccoccocccoococCococ: OcCOOO .oocoCCOOOOO88888O88OOOOoooccCCOOCOCCCCCOCCOOO888OOOO88OOOOOOOCOCCCCCCoooC::oO@OC88OC8o
c:cccccccoocccocooooooooo 8CoO88 :ccccCOOOOOO8888888OOOOOooocoCCOOOOOCoCCOCCOOOO888OO888OOOOOOOOOCCCCCCCCoCc.oO@8O88OOOC
cccccccccooccccccooooCcoo 8OoO8O .::coCOCOOOO888888888O88cocoCCOOOOOCCoCCCOOOOO88888888O8OOOOOOCCCCCCCoCooC:.CO@@8888OC8
cccccccccooccocooooooCooC 8CcOOC .::coCOOOOOO88O8O8888888cocCOCOO8OOCCoCCOCCOOO8O888888O8OOO8OOOCOCCCCCoooo..CO8@8888Cc@
c::cccc:ooccccocccCcoccCC.ooC88o.:.:ocCOOOO888888888888OoocCOOOO8OCOOOooOCCC88888888O8O88OOOOOOOOCCoCCoCooo..OOOO888OcC
c:cccccccocccccoooCooocoC:cCO88:. .:coCOOOO888888888OOOCoooCOOO8O8OOOCooCCCCO888O88888888OOOOOOOOCCCoooooo:.:88888OOOc@@
::cccccccccccocccoooooCCCcc8OCOc ..::oCCOOO88888888OOOOCooCCOCOO8OOOOOooCCCoO888888888888OOOOOOCCOCCCCooC:.:c8888CCCCC@@
:::c:ccccccoccoccCooooooCCoOCOOc ...:oOCOO888888O88OOOCoooCOOOOO8OOOOOCoCCCCoO888888888888OOOOOOOOOCCCooC:..cO88OCOOoC@
::c:cccccccocccccocoooooCocOOOOo. ..:oCOOOO88888O88OOCoooCCOOO8888OOOOCoCCOCoOOOO88888O88888OOOOOOCCoooccc..COOOoo8CcO@
::c:c::occcccccccoooooooCo:OCO8C ..:cCCO88888888OOOOOoCoCCOO8@888OOOOCCCCOCoOOOO888888888OOOOOOOCCoCoCc::. CCCCCCCCc@8
:cc:ccccccccccccoccccooooC :888c ...:ooCCOOOOOOOOOOCOCcCCoCCO88888OOOOCOCOOCoCOOOOO888888888OOOOCCCooocc:.: O88OCo8oC8@
:ccc::ccccocccccocccocoooC :8O . .:.:cOCOOOOOOOOCOCOCcoCcoCOOO88OOOCCCCOOOOoOO88OOO888OO8O88OOOOCoooo:c:. 888OOC8:888
c::c:ccccccccccoccocoooooC .::.:oCOOCO8OOOOCCCCo:coocCOOOOOOOCOCCOOCOOoOOOOOOO888O888OOOOOOCcooo:c:.. 888OCCC:@@88
c::ccccccccccccccccoooooooc .::.:CoCOCCOOCocooCo:c::c:cCOOOOCOCoCCCCCOCoCOOOOOO888888OOOOOCoCCccc::c.. @8O8CC:C@888
c::::cccccccccoccococoooocCCc.. . :ccCoCoOc:.oOo:..c::.::cOOOOOCcoooooCccooCOOOOOO888888OOOOOooCccc..c.. 888OOC:@@888
ccc::cc:ccoccccocccoccoococoCc: .::ooCOCo:.coc:...:...:ccCOCOocoCCoooccCcoCCCOOOO888OO8OCCOOC:occ:: .. .888O8Co@8888
::c:ccccccccccccccocccoccoccc:.. ..:Ccccccc:cc:::::::::.:cccooccCOoC:.co:.::cocCoCCOOOOOOOOoooCo:C:.. .. oOOOO8C@8888@
c:::cccccccccoccccoccoccccc:c.. ..o.cc.::..:::.::c:..:::ccCOoCOc:c:c::::c:c::CooCO8OOOOOOCcc::::c.... oCOOOOo88O888
:::c:c:cccccccc:ccoccoccc:.... ....c.::::.cc:c:::C:...:.coCoccoc::c:.:c:...:c.CooooCOCOOCCCoO::.:::.:. OOCOOCo88888C
::cccc:cccccccccccoccoc:::::.: . ..::::...::o:.:::o ::c..CCcc.:oc:c::..:c:: :o.:cco:ooCOCCCCoc:::. c .. :OOOOO.c888OOC
c::ccc::cccccoc:coccoo::::::. . :.:c.::::c.:..:..:::::oo:c::::cccc:.:c:..:o..cocc:oOCooooco::... . :8O88: O8888OC
::::::c:cccc:c:ccocco:::::.. . .:.:.:::::oOC.::.co ::c:cc:::.coccoc....:::c:.coooccoCCcCcC::...: .:.. c8O. C88O8OOO
::::c:cc:ccc:cccoc:::..::. ... ...::.::cCc::oc::.::.:.Ccc::.cccco.:.: :..:c::cccc::oCccco.:...c.:... C8O8OOOOO
c::c:cc:c:ccccc::..... .. .::co:.:C::.cccC::o.:ooccocccOc:c:c::.:.:::::ccc::::cccc:::.:.:. . . .OCo8@8CCOO8COC
::c::cc:c::cccc::.: .. . ..::::. :::oCc:co.cocccc:oocccCc:co:::c.::c:.:cCc::Oc.:o:::: ..:. . :@8@OOOOOC8OOOO
::c:::cc:ccccc:.... . ..::c..c::ccCCoo.ccoco.ccoooccCooC:c:c:::co:cco.:.cc:ccc:.c..... ... c@OOOOCCOCOOCCO
:c:::::cc:c:::.... .. . .c:o.:c::cCoCCoo:o::oCcccCcOoCoco:ccoc:ocoCccC:cCcc.cc:::::. :. .. o8OOOCOCOOCCCCO
::::::::::::::... .:...... .:co.o::cCoCCCoooooo:coCoCoOcoCoooCoCoc:c:cccccc::c:.:.c..c: .: . CO8OOCCCO8CCCOO
c::::::::::....:. .:::.. .::::.:coc:oOCCoooCococoooCooOOCooo:::ccoCo:cc::.o::c:.:.:c: .. COOCCOCOOOCCCCC
:::::::...... .:: ...:c:.::coCCCOCCoooooCooooocoooooooOooooOOCoco:c:.o::::.:::..:. .. oOOCCOCCOCCCCCCC
::::::..... . .oc . ... ::o ..ccoCoCCCCCCooooOCCCooCoooCooooooCOCOOc.:c..o:.c: ..: .... OCCOOCCCCCCCCCCC
c:::......... :c. : :.c ...:cooCCOCCCCoooCCoCoCCooCoCoCoooOOCoCc::c:cc:..::..: . . . cCCOOCCCCCCOCCCCC
:::.. ..:.. .o: : :::.....cooCoCCCCCOCooCCCCCCCCCoooooCOOCOooc::oc.:::.o:.: ... . CCCOCCCCOCCCCCCoo
::... .:.. :. .: ... o:cooCCoCCCOCCoCCCCCCoCooCoCCCOCOOocCo.:c.:.: ...c .. . :COCCCCCCCCCCCCCoC
......:.. ..: .c. .:: :o::ccoooCCoCCCOCCCCCCCoCOOOOOOCCCoccCc.:::..: .... .. CCCCCCCCoCCCCCCoCC
.. .... ::.. :Cc .. .. ..ooccoOccoococoCoooCOCCCOCCCCCooo::oo.:::::. .... . CCCCCCCoCCoCooooCo
... ::.. . . cC: ...o .: :::CoccCcoo:coooCcCCCCCoCOCoCooc:cc .:..:.. . . .oCCCCCCoCoCooCoooo
.. . ... .. oCc .. ..... : :ccccc:cc:cCooccooCcocooooo:co.c: ..:... . oCCCCCCCCoCCCoooooo
. ... .. .... .oCo. . .: .... c:c:cc:coc:c:cccccccoccccc:c:::c.. :: .. . .cCCCCoooCooCCCoCoooc
...:.. .... .... .:oCC. .:... .c.c:.:c:o::co.cco:ccccccccoc:.::: : :o . cCoOooCoooCoCoooooocc
.:.... ..... .. .:... .C.coCc . ..: . :: o. .::c..cc:::.:cccccc:ccc ...:. .: . . . cOoCCooCCoCoCCooooooo
........:::..::.:. :@8:oCCC:. .. .. ..:. ... .. .. .. ..::..:..::.:..:...... . :.cooooooooooooCccoococc
. . ...:cc.::c.. . @C:ooCCo. . : :: ... ...:. :. .... ....:. ..::: .. cC.oCooooooocCooocCoooooo
. ...::C:.:.:c... .8@@C:oCCCC. . . .. .. . co: o: c.: .... .:. : ... :. Oo:ooooccoooooooocooocooo
...:cc::.:c::... @88OcCooCC. .. . . . . :::cc:.: c..c:............ :. cC:cooocooCooooccooooCcooo
. ....::.:::.. @888coooCCc. . .... . ..cc:Oc:.:c.: cC:: : .... .:... . .. .COo:oCccoooooooooooooocccco
:. .:.:. . C8@8o:ooCCOo .... :.:.::cCcoo.C:c.:c.: c:.. ...:. : cCCo:occoocococoooooccccccoc
. ... .. .88O8CoCoCCCo:. . . .:ccoccC::o:.c: .:::o ......... COCCo:cCcoCoocooccccccococcccc
.. c@88OooOCCCCO:. . . .. . .c:.cCc:.::oo:..co:.. ...... . . cOCCCo:coccoocooccccccocccccccc
8@8OO@oCCCCCCCo.. . .... . .:..o:c:..::o. oc.. :. .. .. OCCCCo:ccoocoocccoooccccccccccc
. .. o88C8@ooCOOoCCOc. .. . ...::.:.cc.. :o:.o:: o. :... :cOCCooC:cccoccccccooococcocccccc
... @@88o@OoCCOOCCCCOc . . . ...:.:..:::.:.cc.:o.: ... ..... . :C8CCoCoCccocccccoccccococcccccccc
... :@88COOCCCOOOCCCCC: . . . :: :.:cc .:.:o ..c.::. . : .oOOCCCoOcoccccccccccococcccccccccc
. 8@88C8@CoOOOCOOCCCoCc:.. .. ... ..:c::.:.::...:.:.... . OOOCCCCoC.occcccccccccccocccccccccc
. . . .. 888@O@@oCOOOOOOOCCCocoo: .. : :.:.:::: ::.:. : . COCCOCoCCOc .occccccccccccccccccccccc
. . .. . .. c@88@O@oCOOCOOOOoCooooCCc. ..:. .. ..::..:.......: . : cOCCOCOCOCC: .occcoccccccccccccccccccc
.. ..:. .. C@888@8@8oOCOOOOOOoCoooCCCOC .: :.... :...... .. .. ... cOCOCOCoCCoC. oococcc:cccocccccccccccc
... ... ... @@@@88@@8oOOOOOOOOCoCooCCCC8C:. . :.....:.. .. . . .ccoOCOOOCCCooCC :ococccccccccccccccccccc
.... ... . ..c@@8@8@@8COOOOOOOOOooCoooOCO88Oo: . . :o..:: . . .. :oOOCCCOOCCOCCCCC. occccccoocccccccccccccc
.... .. .. ... @@@@@O@@8oOOOOOOOOOCoCoCoCOOOO8OOOC:. .. :. .. ...:COCCoOOOCOOOCCCoC. cocccccccccccc:ccccc:cc
... . . . . .... @@@@8@O@8OOOOOOOOOCCCcCCoOOOOO8888888888C:.:.:::::COCCOOOOOOOOOOOOOCCCco8 occccocc:c::::cc::c:cc
. :. ..... .. .@@@@@8O@OO8O8OO8OOOCCCCCCCOOO8O888888888888O88OOOOOOOOCOOOOOOOOOOOCCCoc8O . .occcc:cc:c::::c:cc:c:
. . . .... .... C@@@@@88@OO88888OOOOOOCooCCOOO88O88O88O8OO8OO8OOOCOOOOOOOOOCOO8OCOOOCC:o8C :c:ooccc:c:::c:cc::::
. . ... .. @@@@8@8@@@CO8O8OO8OOOCCCCoCOOOO88888O88O8OO8O8OOOOOOCOCOOOCOO88OOOOOCCOoC8: occcccc:ccc:c::::cc:
. ... ... .. o@@@@@@8@@@OO8888888OOOOCOCCCCOOOO8OO8OOO8O8OOOOOOCCOCCOOCOO888COOOOCCOoOC8 :oc::cc:cc:cc:::::::
. ..... ...... @@@@@@@8@@@CO8888888OOOCCOOCCCOOOOOO8OO8OOOOOOOOOOCCOOOOCOOOOOOOOOOOOOCCCOC . :ccc:::::cc::::::::
. . ... .... C@@@@@@8O@@OO88888888OOOCCCOooCOOOOOOOCCOOOOCO8OOOOCoOOOOOOOOOOOOOOOOC@@CO c:c:cc:c::::::::::
.: .... .. @@@@@@888OOO888888888OOOCCOCoC88OOOOOOOOCOCO8OOCOCOOOO88OOOOOOOOOOoOOOc . cc:::c::::::::::::
.c ... ...... :@@@@@@8@@COO888888888OOOOOOCCoOOOOOOOOOOO8OOCOOOCOOOOOOOOOO8OOOOOCC8OO. .oc:::::::::::::::
.c... .. ... @@@@@@O@@@@OO88888888888OOOOOOOCoCCCCCCOOOOOOOOOOOOOOOOOOOOO8OOOOOCO@@COc .c:::c::::::::::
Oo . ...... C@@@@@@88@@OO88888888888OOOOOOOOCCCCOOOOOOOCOOOOOOOOOOOOOOOOOOO8OOO@CC8 .c:::::::::::::
oc .. . .....@@@@@@@88@@@O8888888888O8OO8OOOOOOCCOCOOOOOOOOOOOOOOOO8OOO8O88888OC@@CO88 .c::::::::::::
Made with soft by Håkon Nessjøen from http://lunatic.no/img2aschtml.php.
Subscribe to:
Posts (Atom)